
As businesses enhance their risk management techniques, the importance of efficient audit procedures and robust internal controls cannot be overstated. Audit procedures are used by audit teams to identify and assess risks. Auditors can also recommend mitigation, such as a control effectiveness deficiency that could impact an organization’s operations and financial health.
But how do audit procedures and internal controls impact the overall assessment of controls for external audits? By auditing the effectiveness of internal controls, auditors can identify gaps in processes and controls that could later impact external audits and result in potential findings. Let’s explore.
How audit procedures and internal controls go hand-in-hand
Audit procedures and internal controls have a symbiotic relationship. Supporting each other, they are two pieces of the puzzle that is successful risk management programs. By auditing control effectiveness internally first, auditors can better prepare for external audit procedures and acknowledge where improvements need to be made before auditing against certain frameworks.
But first, we need to understand what audit procedures and internal controls are and how they relate to each other.
What are internal controls?
Internal controls protect companies from various risks, such as financial, operational, strategic, and reputational risks. They serve as a means to protect the organization and adhere to certain standards and frameworks so that companies can pass audits and achieve compliance certification. Examples of these audited frameworks include SOC 2® and ISO 27001.
Components of internal controls
The Committee of Sponsoring Organizations of the Treadway Commission (COSO) framework defines the components of internal controls as the following:

The control environment
The control environment is the foundation for all other components of internal control. It provides the discipline and structure necessary for the effective implementation of internal controls within an organization.
Risk assessment
Risk assessment is the process of identifying and analyzing risks that could potentially prevent the organization from achieving its objectives. It involves understanding the internal and external factors that could impact the organization, evaluating the likelihood and impact of these risks, and determining how they should be managed.
Control activities
Control activities are actions taken to mitigate risks and ensure the organization’s objectives are achieved. These activities occur at all levels and functions of the organization and are designed to prevent or detect errors and fraud and ensure compliance with policies and regulations.
Information and communication
Information and communication are critical components of internal controls that ensure the organization’s relevant information is identified, captured, and communicated in a timely manner to enable people to carry out their responsibilities.
Monitoring
Monitoring is the process of assessing the quality of the internal control system over time. This involves regular evaluations to ensure that internal controls function effectively and deficiencies are promptly identified and addressed.
What is control testing?
Control testing is an essential part of risk management, especially in the context of risk management audits. Testing controls helps you understand if your company’s controls are properly designed, implemented, and operating effectively to mitigate identified risks.
These tests are crucial to the audit process and provide assurance that the controls in place are adequate to manage the organization’s risks.
What are audit procedures?
Audit procedures encompass auditors’ steps, processes, and methods for examining and assessing audit evidence. Whether internal or external, auditors must follow certain procedures to perform an audit properly.
These procedures are the basis of test procedures. An auditor will often pick one or two types of audit procedures and use those to design their test procedures. Not all audit procedures are used in all tests.
These six steps encompass what you need to know to follow audit procedures. Please note that internal auditing is an ongoing, iterative process that often requires you to follow a repeating cycle of steps, much like the risk management process itself. An external audit is more of a point-in-time event.

1. Inspection
Inspection involves examining documents, records, and physical assets to gather evidence about the effectiveness of controls within the organization.
Examples include document and record inspection, as well as physical asset inspection. Through these inspection activities, auditors gather critical evidence to assess whether the organization’s controls are effectively designed and operating as intended.
2. Observation
Observation involves watching processes and activities as they occur to gather evidence about the effectiveness of a company’s internal controls.
Examples include the observation of physical security measures or processes and procedures. With observation procedures, auditors gain firsthand insight into the practical implementation and effectiveness of the organization’s controls.
3. Confirmation
Confirmation involves obtaining direct verification from third parties or internal stakeholders about specific information or conditions to gather evidence about the controls and their effectiveness.
Examples include confirmation from external parties and from internal stakeholders. Auditors obtain third-party and internal verifications via confirmation activities that provide critical evidence about the effectiveness and reliability of the organization’s risk management practices.
4. Reperformance
Reperformance involves independently executing the procedures and controls initially performed by the organization’s personnel to validate their effectiveness and accuracy.
Examples include reperforming control activities, risk assessments, and compliance procedures. Reperformance allows auditors to validate the effectiveness and accuracy of the organization’s risk management controls and procedures, ensuring they function as intended and provide reliable protection against identified risks.
5. Analytical procedures
Analytical procedures involve evaluating financial and non-financial information through analysis and comparison to identify unusual trends, variances, or relationships that may indicate risks or areas needing further investigation.
Examples include trend analysis, ratio analysis, comparative analysis, and reasonableness tests. Auditors can identify unusual patterns, trends, and variances that may indicate areas of risk or concern, allowing for targeted follow-up and deeper investigation into the organization’s risk management practices.
6. Inquiry
Inquiry involves asking questions of knowledgeable individuals within and outside the organization to better understand the risk management processes, controls, and environment.
Examples include internal inquiries, external inquiries, inquiries into specific risk areas, and follow-up inquiries. By inquiring about various risk-related activities, auditors gain valuable insights and context surrounding the organization’s risk management practices. This allows for a more informed, comprehensive assessment of the effectiveness and reliability of internal controls and processes.
Example of a risk management audit procedure
An example of a risk management audit procedure is the assessment of the effectiveness of internal controls. By conducting these five steps, auditors can provide assurance on the adequacy and effectiveness of the organization’s risk management practices:
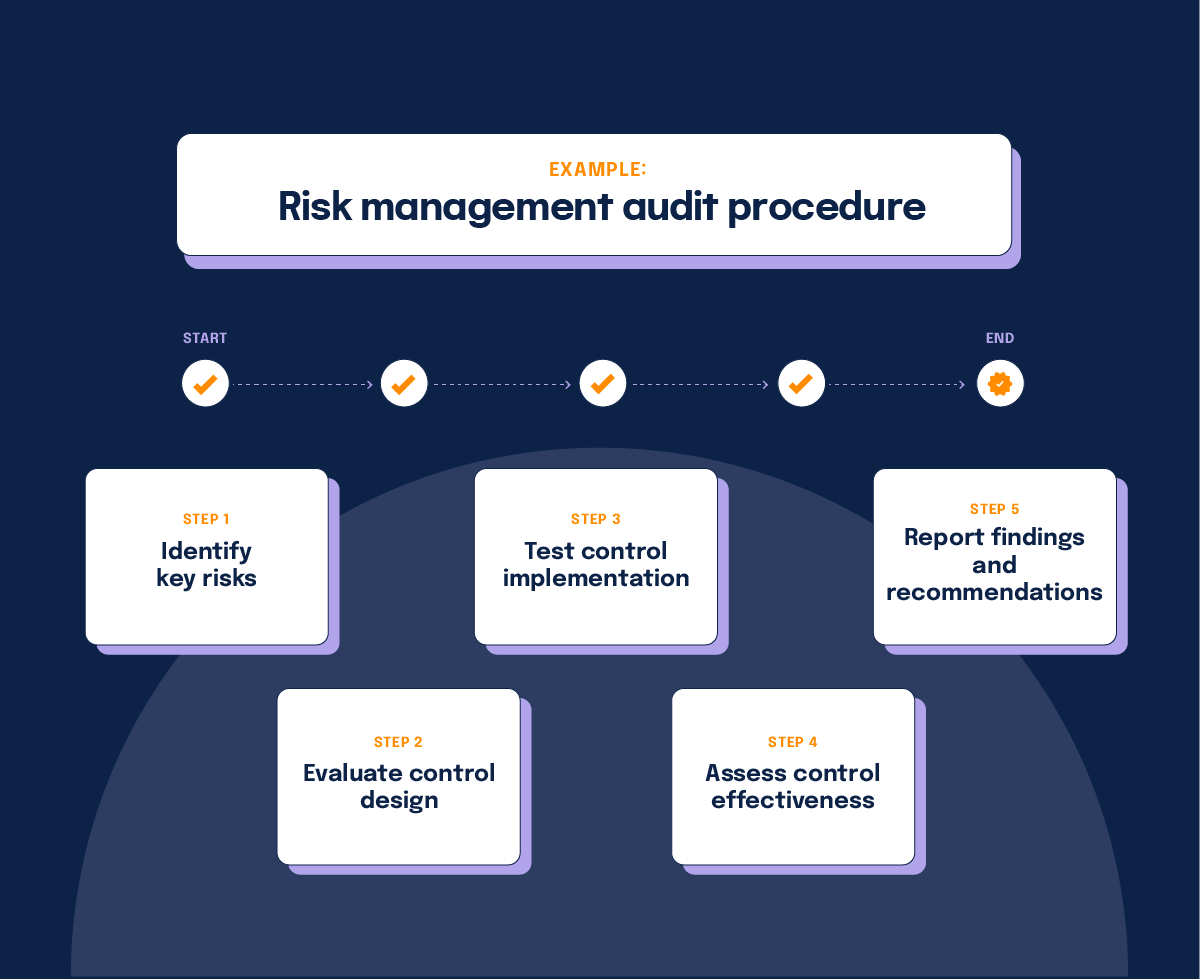
1. Identify key risks
Determine the major risks that could impact the organization’s objectives, such as financial, operational, compliance, or reputational risks.
Note: Some companies may take a different approach and identify their key controls instead. If their program is designed well, the key controls mitigate a larger proportion of the key risks.
2. Evaluate control design
Review the design of the internal controls in place to mitigate identified risks. This includes examining policies, procedures, and documentation.
3. Test control implementation
Perform tests to verify whether the controls are implemented effectively and consistently. This might involve walkthroughs, observations, and sample testing of documents or processes.
4. Access control effectiveness
Analyze the test results to determine whether the controls are functioning as intended and effectively reducing risks to an acceptable level.
5. Report findings and recommendation
Document any deficiencies or weaknesses in the controls and provide recommendations for improving them to strengthen the risk management framework.
When should you use these audit testing procedures?
Each audit testing procedure has specific applications depending on the nature of the audit, the objectives, and the areas evaluated. For example, inspection should be used when you need to verify the existence, accuracy, and completeness of documents, records, and physical assets, while analytical procedures should be used when you need to identify unusual trends, variances, or relationships in financial and non-financial data.
By appropriately using these audit testing procedures, auditors can ensure a comprehensive and effective assessment of an organization’s risk management practices and controls.
How audit procedures and internal controls work together
Example
Take a large multinational financial institution. An audit will help ensure that their cybersecurity controls are effective in protecting sensitive data and preventing unauthorized access and cyberattacks.
Action: The financial institution must conduct a risk assessment to identify critical cybersecurity threats, such as data breaches, unauthorized access, phishing attempts, and malware infections. Outcome: A comprehensive list of key risks that the financial institution needs to mitigate to protect its sensitive data and systems.1. Identify key risks
Action: The financial company must then review the design of existing cybersecurity controls, including access controls, data encryption, incident response plans, security audits, and continuous monitoring. Outcome: An understanding of how well the controls are designed to address the identified risks. For example, multi-factor authentication (MFA) for access control, encryption protocols for data protection, and a detailed incident response plan.2. Evaluate the control design
Action: The financial institution’s auditor will then perform audit procedures like inspection, observation, and reperformance to test whether the designed controls are implemented effectively. Inspection is defined as inspecting access logs, MFA configurations, encryption policies, and documentation. Observation is defined as observing a simulated cyber incident response drill and the functioning of the Security Information and Event Management (SIEM) system. Reperformance encompasses independently performing sample penetration tests and security audits to verify the findings of internal teams. Outcome: Evidence that controls are implemented as designed. For example, access logs show that MFA is being used and the SIEM system is actively monitoring network activity.3. Test control implementation
Action: The auditor will then analyze the results of control implementation tests and use analytical procedures to identify trends and patterns in security incidents. Analytical procedures are defined as the analysis of historical data from security incidents, audit reports, and penetration tests to detect recurring issues or emerging threats. Outcome: Assessment of whether the controls effectively mitigate the identified risks. For example, the analysis might reveal that although MFA is implemented, there are still incidents of unauthorized access due to phishing attacks, indicating a need for additional controls or training.4. Assess control effectiveness
Action: Lastly, the auditor will then compile the findings from the audit procedures and assessments into a report, highlighting any deficiencies or areas for improvement. Inquiries are defined as interviewing IT security personnel about the implementation, updates, and monitoring processes for cybersecurity controls. Outcome: A detailed audit report that provides recommendations for strengthening cybersecurity controls. For example, the report may recommend enhancing employee training on phishing awareness, updating encryption protocols, or improving the incident response plan.5. Report findings and recommendations
Audit procedures made easy with Hyperproof
Audit procedures outline the how, what, and why of auditing. Paired with internal controls, audits can help you assess your organization’s compliance and security posture. By acing audits, you prove to the world — and your customers — that you’re ready for what may come your way.
Creating the optimal audit experience benefits many stakeholders. By consolidating all of your work into a unified risk management and compliance platform, you can simplify the audit process and save hours of time on audit preparation.

In fact, one of our customers reduced their audit prep time by 50%, resulting in a more efficient audit experience. With automated evidence collection, dashboards showing audit progress, and personalized invites to their external auditors, they crafted a streamlined audit experience with Hyperproof.
Hyperproof can help accelerate your audit process by connecting audit requests automatically to your controls and associated evidence. Use Hyperproof’s dedicated audit space to invite your auditor to work alongside your team — making information sharing easy and keeping access to only what they need. Plus, assign specific evidence requests from your auditor directly to your team members, so they can communicate directly, reduce friction, and speed the audit process up.

Ready to learn more?
Get a Demo